how to log a data breach
According to the GDPR legislation an organization must report a data breach to a data protection authority DPA also known as a. Some online services allow you to view what devices have recently used your login details and any recent transactions.
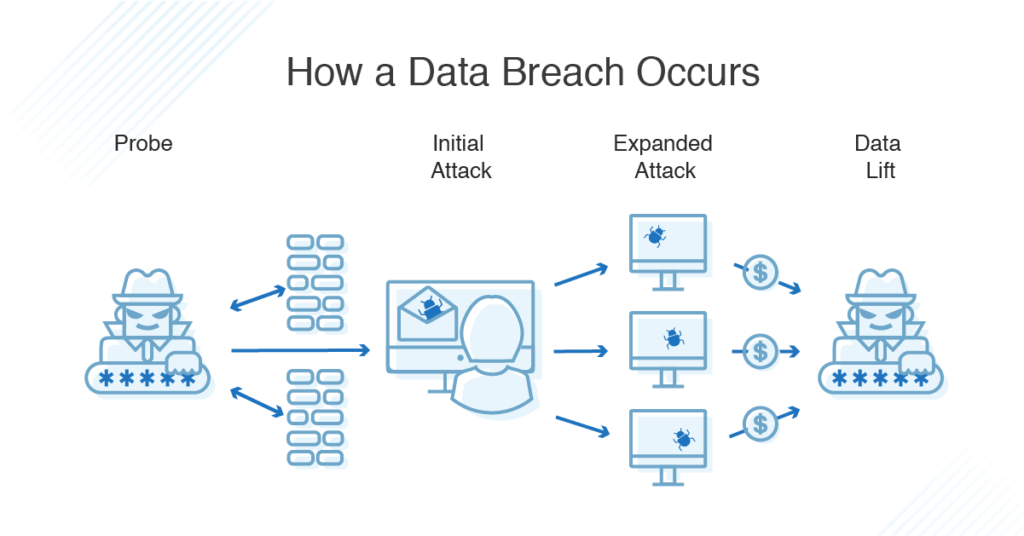
What Is A Data Breach Definition Types Dnsstuff
2 hours agoBy Jacob Kastrenakes jake_k Jun 6 2022 933am EDT.

. Make sure the new password is secure. A data breach is when your personal data is accessed copied or changed by someone without your permission. Ad Secure your enterprise.
Data loss a mystery. Current Data Breach Methods. You can usually also log out those devices from these settings.
The DBIR 2020 lists nine core clusters of incidence classification patterns which account for about 88 of data breaches. Elon Musk says that Twitter is in clear material breach of. A data breach occurs when a companys or individuals stored data is accessed or open to access by unauthorized parties.
The log should describe the incident itself the cause repercussions risk of future damage. These incidents can be intentional such as a. Ask your forensics experts and law enforcement when it is reasonable to resume regular operations.
The log should describe the incident. Mobilize your breach response team right away to prevent additional data loss. First you have to record the date and time you identified the data breach.
Sometimes a data breach involves financial information including credit card numbers or bank account information. If your Social Security number or financial information was part of a data breach freezing your credit will restrict access to it which makes it challenging for. Dont wipe and re-install your systems yet Do follow your incident response plan.
You should act on this type of breach as soon as. Data breaches are extremely. We have a process to inform affected individuals about a.
Review logs to determine who had access to the data at the time of the breach. Maintaining the integrity and ensuring a provable chain of custody of digital. A data breach is a security violation or incident that leads to the theft of sensitive or critical data or its exposure to an unauthorized party.
Reconstructing the events that led to a security breach or compromise using security log data. Check data breach websites. Confirm the breach has happened but be cautious of emails Find out what sensitive data was stolen and is available to hackers.
The Breach Notification Law MGL. An email data breach can happen when there are security issues with an email. The data breach reporting forms can be detailed and involved so prepare as much information as possible ahead of time so that this form can be filled out quickly and.
One of the best ways to check if you have been hacked is to enter your email into a number of data breach websites that track breaches and. 3 requires that a person or agency including public and private entities that maintains stores owns or licenses data that includes personal. Analyzing logs is the primary way of doing forensics and properly managed logs can also be used as evidence in a court of law for prosecution purposes.
Many data breaches will affect your passwords even if it also affects other data. GDPR requires all firms to keep a log of any and all breaches even the smallest incidents should be recorded. Illustration by Kristen Radtke The Verge.
Responding to a personal data breach We have in place a process to assess the likely risk to individuals as a result of a breach. Meaning cybercriminals can gain access to your information through an organisation website. Most data breaches involve hacked email accounts and.
Follow These 8 Steps After a Data Breach. To prepare for a data breach event policies actions and tools can be put in place to lay out a plan for detecting and containing an. A data breach is a security violation or incident that leads to the theft of sensitive or critical data or its.
When to report a data breach under GDPR. Data Breach Incident Log Template. Freeze Your Credit.
Be sure to log into the affected accounts to change your password. Discover the core of identity security. They are the common.
Doing it right has moved beyond human capacity. Your first priority at this point in time is to isolate the affected system s to prevent. Implement tools services and policies.
Hackers breaking into a storage server to steal. A data breach occurs when cybercriminals steal information from an organizations database without permission from the owner or administrator.
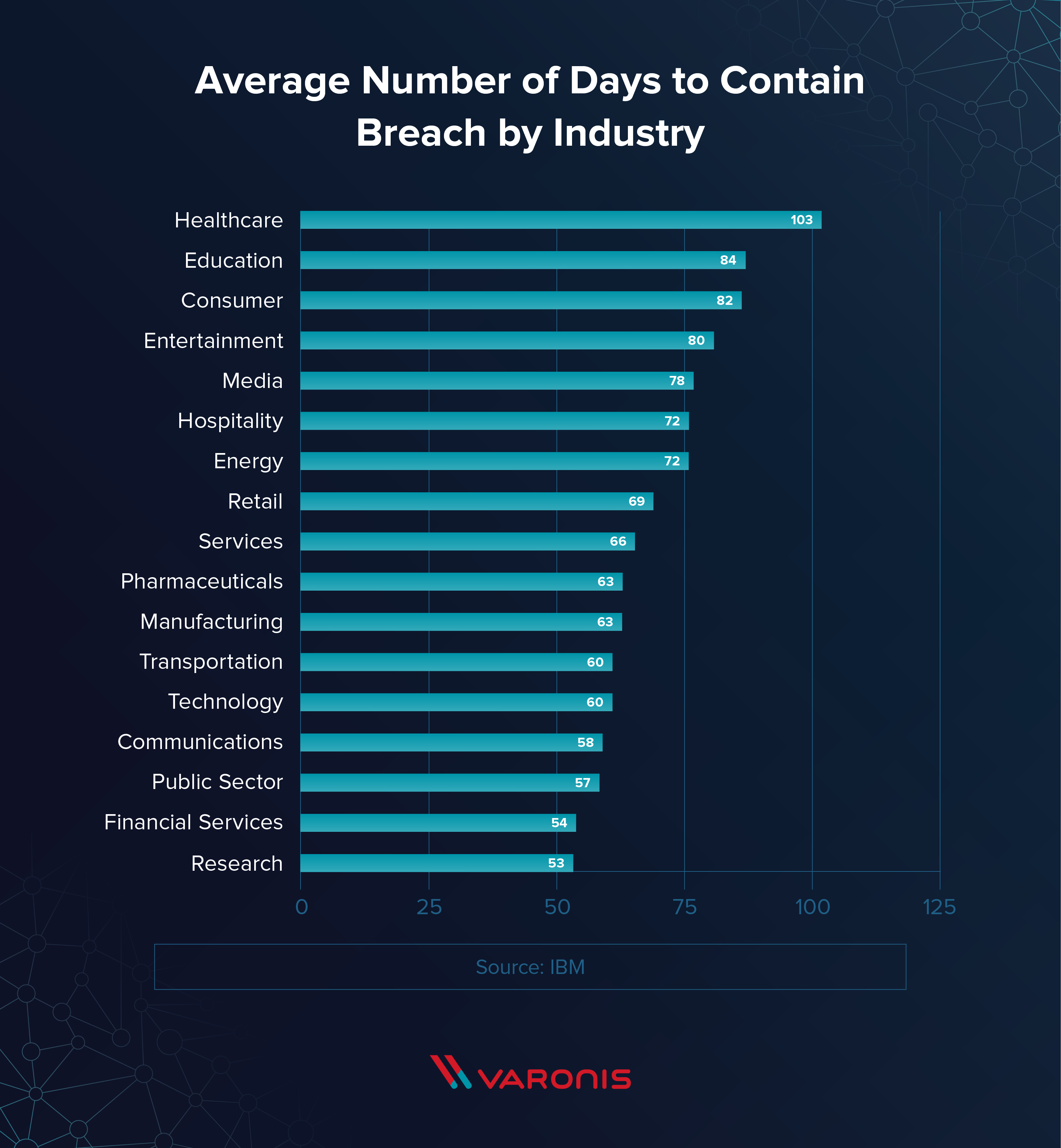
Data Breach Response Times Trends And Tips

Common Data Breach Causes Cyber Security Awareness Infographic Marketing Data Breach

Pin On Information Security Cyber Tip Posters

Data Breaches In The Financial Service Industry Rise In 2016 Fintech Security Data Breach Infographic Cyber Security

Onelogin Businesses Vulnerable To Data Breaches By Ex Employees Data Breach Data Vulnerability

Login With Facebook Data Hijacked By Javascript Trackers Techcrunch Data Marketing Insights Tracker

Impact Of Data Breach On The Legal Industry Infographic Data Breach Productivity Infographic Social Media Infographic

Handling Data Breaches In Your Business Privacy Policies

Known Data Breaches Heavy Fines Ahead Data Breach World Data Big Data

How To Deal With A Data Breach Of Your Personal Info Privacy Policies

Data Breach Response Times Trends And Tips

5 Steps To Take After A Small Business Data Breach Whoa Com

7 Key Steps To Investigate A Data Breach With Checklist Ekran System

How To Write Gdpr Compliant Data Breach Notification Letters Privacy Policies
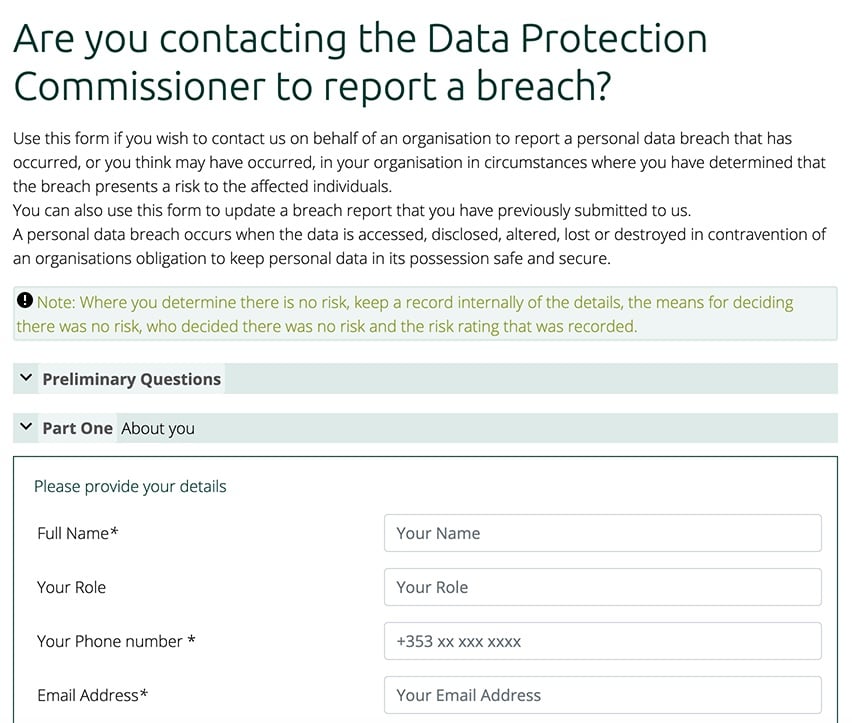
How To Write Gdpr Compliant Data Breach Notification Letters Privacy Policies

Data Breach Infographic Data Breach Shocking Facts Infographic

How To Avoid Getting Sued For A Data Breach Insureon

How To Write Gdpr Compliant Data Breach Notification Letters Privacy Policies

7 Key Steps To Investigate A Data Breach With Checklist Ekran System